When you purchase a product online your personal and private data is your product you give away in exchange for convenience and “free” shipping. Every step in the process is an opportunity to data mine your privacy.
Countless details about you are collected, compiled, categorized, and mapped with other data aggregating services. A digital dossier about you is for sale to the highest payer. This information can be exploited by hackers, high tech employees, civil and criminal legal processes and nation states.
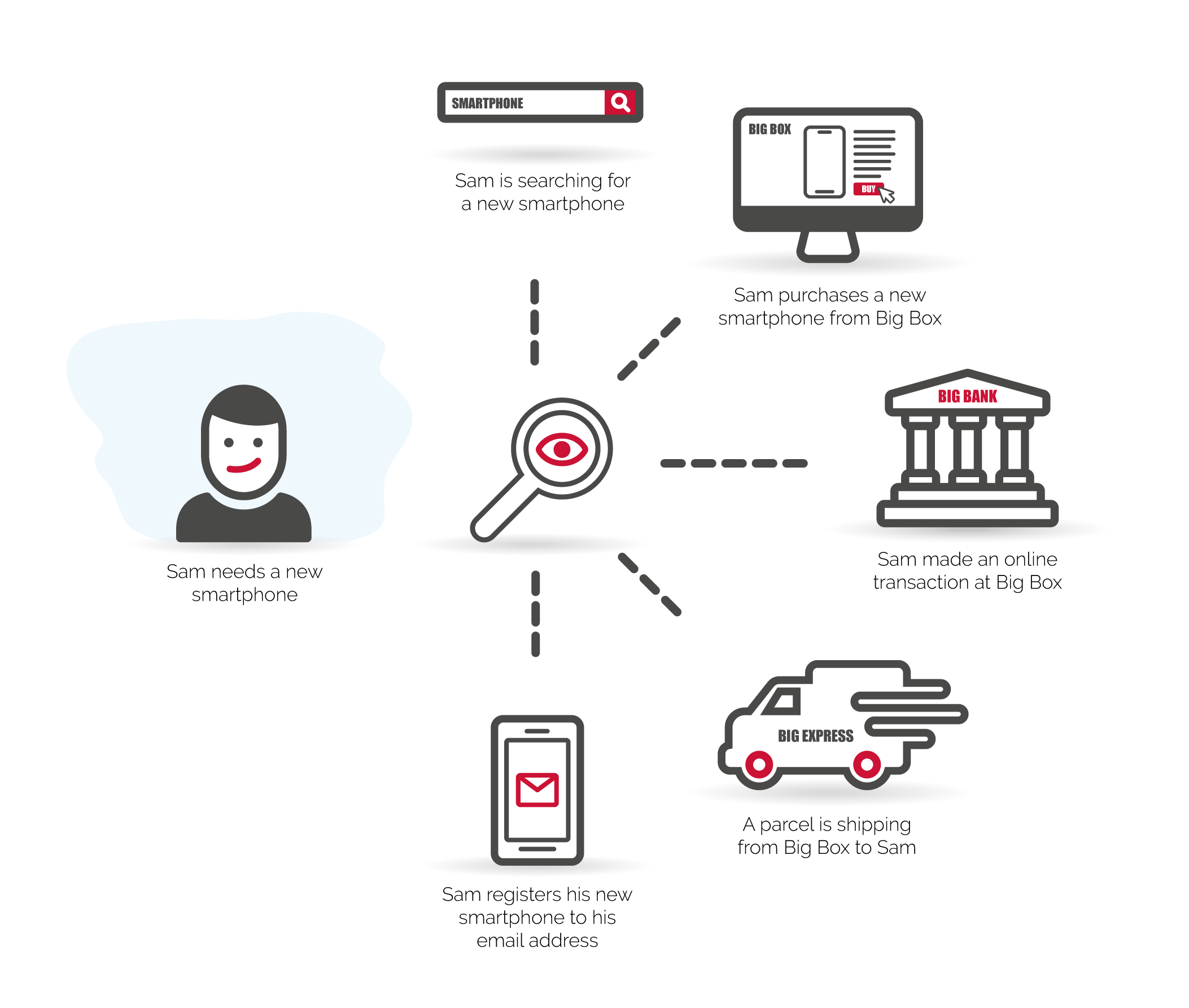
Tools and techniques are available to improve e-commerce privacy. However, they are fragmented, regulated, and vulnerable to targeted exploitation. You the consumer may never be informed your data is being exposed and shared with other services or agencies. Extreme situations occur where electronic items are secretly intercepted en route and compromised turning your purchase into a spying device.
PrivacyPost.io is the customer of record and proxy for your purchases and shipping.
Your shopping details are obfuscated with several other purchases. You become a smaller needle in a larger haystack. Membership options offer many privacy enhancements including a unique tamper evident process ensuring your electronic items were not intercepted en route and compromised to spy on you.
Our purpose is to provide a secure and private supply chain protecting you from invasive analytics, surveillance capitalism, and Big Brother back doors.
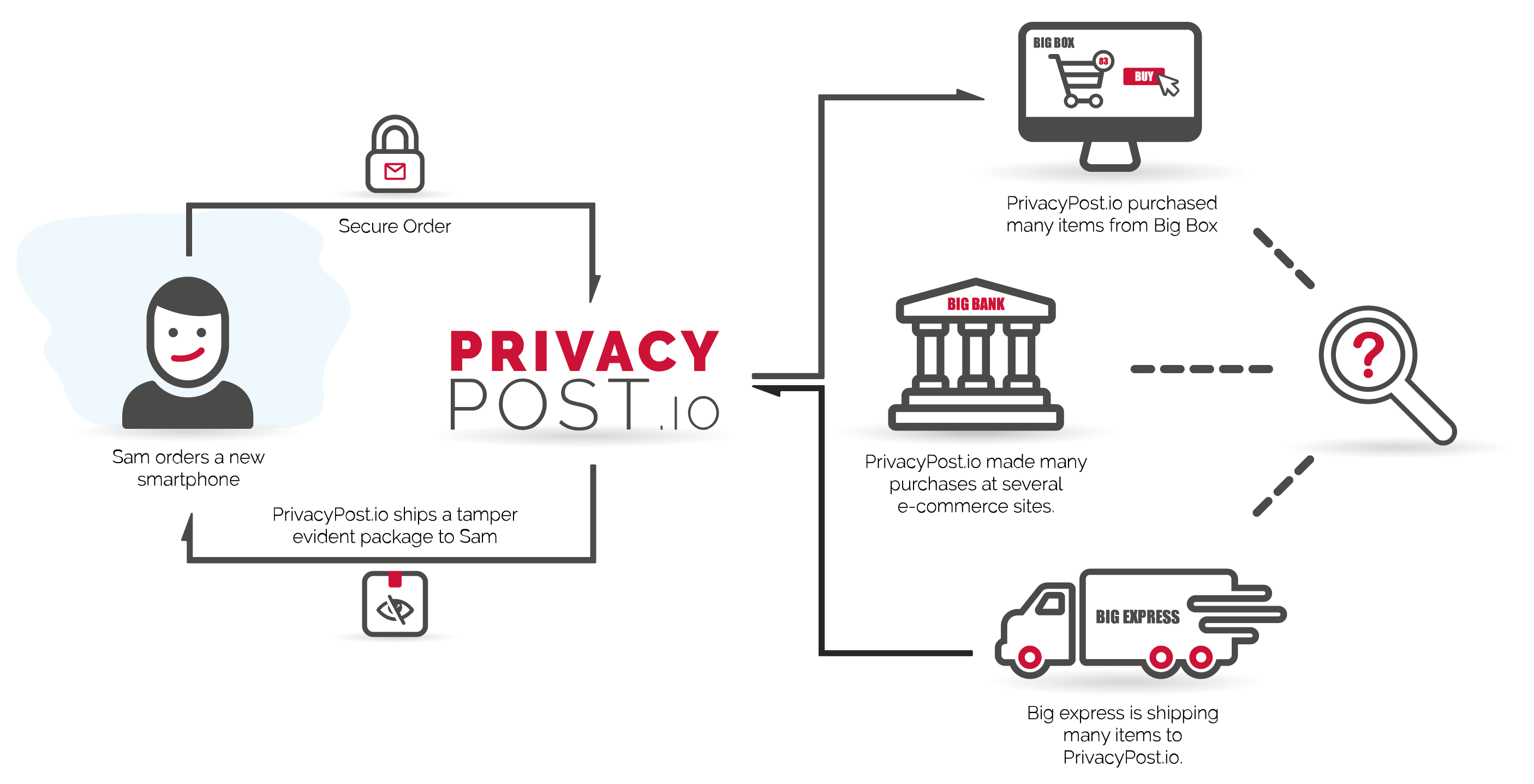
Your purchasing details are retained for the transaction period then shredded for good. The only thing known is that PrivacyPost.io sent you a package. This can also be anonymized by providing an alternate shipping address not associated to you.
PrivacyPost.io is a membership based service. Due to our privacy enhanced payment model, memberships are purchased annually.
|
|
|
|||||
|
PRIVACY $0/month
|
PRIVACY + $6/month
|
|||||
|
|
|
|||||
|
PRIMACY $11/month
|
PRIMACY PRO COMING SOON
|
|||||
|
|
||
|
PRIVACY $0/month
|
||
|
|
||
|
PRIVACY + $6/month
|
||
|
|
||
|
PRIMACY $11/month
|
||
|
|
||
|
PRIMACY PRO COMMING SOON
|
||
* Denotes extra fees

Any non-bidding e-commerce website item conforming to our shipping rules and ethics. E-Bay is supported as long as it is a “Pay Now” item. Looking for a specific item or e-commerce website? Contact your privacy consultant for guidance.


|

|

|

|

|

|






|

Primacy members have the option to have an item purchased at a local store. This is commonly used for technology purchases to anonymize setup and mitigate supply chain attacks or interdiction prior to our tamper detection process.
An example would be the purchase of a new iPhone. PrivacyPost.io will purchase with cash at a local Apple store. Optionally we would configure the phone with a privacy protected process and ship to the member. Review the VIP services page here.
Are you stuck in a privacy loop? You want to sign up for a privacy app to improve your privacy but you do not want to expose your personal information in the sign up or payment process? You then try to establish a private payment method but you need a privacy app to establish the private payment method? Getting stuck in this privacy loop is a common challenge for people hardening their privacy model. We can help you start on the right track. We will order your privacy service with our credentials then pass the new service on to you. This works perfect for VPN, email and privacy app purchases that are a must as the foundation for your privacy model.


|

|

|

|

|

|

|







|
PrivacyPost.io is building a basic online store for select privacy products. We choose products and vendors that meet our rigid privacy and secure supply chain requirements. We are the fulfillment center for all of these products so no data collecting third parties know your true identity, payment information or package contents. Just to be clear, our shipping vendors will know receiver name and address. However, you can protect your privacy by choosing the destination name and address best fitting your privacy model.

Book
Extreme Privacy: What It Takes to Disappear
$42.00
Pixel 6a with GrapheneOS
100% DeGoogled
Secure load and configuration
$350 Custom Configuration
Primacy membership required

Anonymous SIM
All Providers
Modem Support
No Contracts
World SIM
$18 Per Month and Up
Primacy membership required

Pepwave MAX Transit Router With 1 x Cat 18 LTE Modem + PrimeCare (1yr)
Contact for Pricing
(Price Match Guarantee)
Primacy Membership required
Custom Configuration
SIM card installation and activation
Plug and Play
Advanced support

Cradlepoint CBA850 Cat 18 with NetCloud (1yr)
Contact for Pricing
(Price Match Guarantee)
Primacy Membership required
Custom Configuration
SIM card installation and activation
Plug and Play
Advanced support

4G LTE Stealth Modem CAT 6 or better
Contact for Pricing
White Label
Rotating identifiers
ALL Carriers
SIM card installation and activation
Advanced support
Plug and Play
Primacy Membership required
See Blog post for more details

Unfortunately private and convenient electronic transactions are impossible. We provide options supporting privacy or convenience. You choose what is best for your privacy model. Choosing a non-private payment method does disclose financial transaction details connecting you to PrivacyPost.io. However, what you purchased is only known to you and PrivacyPost.io. Our foundation of extreme privacy, short data retention and canary services, add layers of privacy breaking the chain of surveillance.


We do accept credit cards as payment of last resort with a 4% convenience fee. We do not accept paypal for many reasons. Read our FAQ for more details. Wise is encouraged for U.S. and international bank transfers. PrivacyPost.io advocates their innovative business model. Zelle and Cash App are other fast and convenient alternatives. You may not even be aware of Zelle unless you ask your bank or check here.
We accept crypto payments through any currency supported in the Bitpay wallet and Monero. Monero is offered as an alternative to clients preferring maximum transaction privacy. If you are new to crypto and need assistance we can provide step by step guidance for members or those purchasing a membership.

|
||||

|

|

|

|

|

|
|||

|

|

|

|
PrivacyPost.io supports all standard shipping methods and more. Options are only limited to your membership level, financial resources, and imagination. The name and destination is entirely up to you and can be unique for each order. If you are concerned about shipping privacy please contact a privacy consultant to discuss options or creative solutions.

Primacy and Primacy Pro members will have priority access to a dedicated privacy consultant to discuss privacy concerns and options including out of band shipping. For privacy and opsec reasons we do not publish these methods.

|

|

|

|




|
We keep this is simple as possible.

All shipments must comply with Postal Service regulation or private carrier, restrictions and all U.S. laws and regulations.

We do not purchase or ship firearms or ammunition.

We do not purchase or ship items from the dark web.

PrivacyPost.io is built upon a foundation of privacy. We highly encourage communication from trusted encrypted and privacy respecting services and protocols.
If you are new to private communication and need our help then contact us by phone or unsecured email. We will gladly assist you with your privacy model.
If you are already familiar with private communication, remember to message within the eco-system you choose. For example: Proton ==> Proton or Signal ==> Signal. We are strong supporters of Protonmail. If you are new to privacy we recommend signing up. Never create a username containing any part of your last name or any other identifying information.
![]()
![]()
+1 860-854-1984
![]()

PGP Public Key
![]()
![]()
@privacypost
1 860-854-1984

Our ordering process is designed to be as safe and secure as possible. This is why we do not support form field pdf or docx files. This process will evolve as we progress. Phase one will be a simple downloaded or copy/paste text file.
Downloading a form does provide opportunities for compromise. Our website could be infiltrated and the downloaded form hacked with malicious code. Checking the hash of the downloaded file will help mitigate this concern. If checking the hash value of the form file is too complex for you then use the copy/paste option.
Download Form Option
1. Download form
2. Before opening- Check hash value. The SHA256 hash value is published in several places including here and https://www.reddit.com/r/privacypostIO/
Validate hash value character by character. This is most easily done by copy paste both to a word or text document one placed below the other like this.
27ba49e6e707e953c605abb9f37a2fb86d6e5ad458ead4943c8e77007e96c6fc
27ba49e6e707e953c605abb9f37a2fb86d6e5ad458ead4943c8e77007e96c6fc
If the value is the same it is safe to proceed. If the value is different download again and verify. If the value is still not the same do not open the text file. Move to your trash and empty. Then revert to the cut and paste option. Contact PrivacyPost.io of the error.
3. After the file integrity is verified open it up and fill out the form. Most fields are self explanatory.
4. Save changes to text file
5. Choose the preferred communication method from the contact list. Be mindful the email subject line may not be encrypted. Keep subject line general like “order request”. Make sure to message within the secure platform you choose. Proton to Proton for example. Use only listed contact methods from the contact list. Please no unencrypted gmail or SMS.
6. Attach the order form to the message. Enter any other information in the body of the message.
7. If your selected communication method supports message auto delete set to delete no longer than 30 days.
This will initiate the custom order process and we will respond with more information and details. The remaining order process will be completed through the supported communication method you selected.
Copy and Paste Form Option
1. Choose the preferred communication method from the contact list. Make sure to message within the secure method you choose. Proton to Proton for example. Use only listed contact methods from the contact list. Please no unencrypted gmail or SMS.
2. Start a new conversation to the PrivacyPost contact destination. Be mindful the email subject line may not be encrypted. Keep subject line general like “order request”.
3. Copy/paste the form into the body of the message. Either fill out the fields or if this is too difficult use the form as a template to answer each question below the template.
4. If your selected communication method supports message auto delete set to delete no longer than 30 days.
5. Verify you have the correct destination information for privacy post then send.
This will initiate the custom order process and we will respond with more information and details. The remaining order process will be completed through the supported communication method you selected.
---------------------------------------------------------------------------------
| |
| |
| PRIVACYPOST.io |
| |
| - Copy & Paste Form - |
| Version: 06.21.2020 |
| |
| |
---------------------------------------------------------------------------------
1. Website Name*:
2. Website Country*:
3. I prefer PrivacyPost research the product on my behalf to protect my privacy*
[ ] Yes (Skip 4 and 5) [ ] No
4. Unique Product ID or Code:
5. Displayed Price:
6. Product Description*:
7. Any other specific information like size, color,etc:
8. Destination zip code*:
9. Ship direct from site?*
[ ] Yes [ ] No
10. Amazon Locker?*
[ ] Yes [ ] No
Payment Method*:
[ ] Zelle [ ] Amazon e-gift card
[ ] Wise [ ] Amazon gift card
[ ] ACH [ ] Monero
[ ] Money Order
-------------------------------------
(*) MANDATORY FIELDS
-------
Field 3 is important: Browsing the web provides several opportunities for your searching history to be identified to you.
If you are concerned about leaving breadcrumbs from your product search we can do the searching for you.
Fields 4 and 5: If you do your own product search make sure to complete.
Field 4: Every site has a item number for the product. Most are listed on the product description section.
Every Amazon item has a ASIN number located in the description section. Enter this number here.
Field 8: The zip code is all we need at this stage to calculate shipping costs.
Field 9: If you have a private and anonymous shipping destination shipping direct can save time and additional shipping costs.
Field 10: If you have easy access to a amazon locker mark yes. Consider the several opportunities for you to be identified
including the locker camera, store CCTV, geo fencing, and parking lot ALPR (automatic license plate readers)

We can not emphasize enough our commitment and dedication to customer privacy. Every technology and process we implement is founded on privacy. The PrivacyPost.io website does not retain logs, fingerprint your browser, track your behavior or store any out of the ordinary cookies on your browser. The only data that is exchanged is what is minimally needed to browse our website.
Outside of communication options already clarified, we do not store any of your data on the cloud or use any cloud services. Minimal data about you, what you order and where you ship is retained. Once the order process is complete we shred the detailed data of the transaction. Total privacy is impossible. There are weak links in the payment and shipping process however we do whatever technically and creatively we can do to obfuscate your purchases.


OOur canary protocols are a unique and bold service we provide our customers. We offer two options depending on your membership level. The standard canary service is provided to our Privacy + members. Quarterly you will receive a basic and authenticated email declaring no search warrants have been served associated to your shipping addresses, payment identity, or email address.
Primacy and Primacy Pro members will receive a more detailed email on a monthly schedule. Warrant canaries are not infallible. However, they provide another level of privacy assurance unmatched by any other service.

Our Seppuku pledge is a statement of intent to shut down and cease operations in the event of an unsurpassable order to operate under the supervision, control, or influence of a malicious entity.
Like the warrant canary, the Seppuku pledge is not infallible. Our operations can be seized and we can be suppressed allowing a highly resourced adversary to take over our operations pretending to be us and collecting information about our members. Outside of this unique and unlikely situation, we make this pledge to our customers.

We believe privacy is a human right. Our clients cover a broad spectrum of privacy requirements ranging from keeping their personal life private to the extreme where privacy is required to protect freedom, a way of life or even to prevent political persecution or death. We are true to the client by providing a shield of privacy within the boundaries of all laws. Core business decisions and services are based on this privacy core principal.
We differentiate privacy from secrecy. Privacy is for entities requiring private and discreet product purchases. We regard secrecy as hiding ones behavior for unlawful or harmful reasons. The use of our services for unlawful reasons and intentions to do harm are forbidden.
If we discover a client is a criminal enterprise or operating with criminal intent we will terminate the relationship immediately without explanation.
Our services will not be used to bypass customs and duty tax. Our services will follow all import/export laws. This includes content disclosure and value.
ALL interactions from legal authorities regarding client information requires a warrant. We will not be pressured or intimidated to comply without due process.
Privacy is a marathon not a sprint. It is a incremental process and unique journey for each individual. Any step towards privacy is a step in the right direction. Privacy maximalists and elitists prescribe to certain rigid beliefs and practices and may shame or dismiss others privacy practices. We believe in a inclusive privacy community where all are welcome who desire to improve ones privacy. Our purpose is to promote, educate, inform, and empower privacy.

PrivacyPost.io is where high tech privacy geeks meet old skool shipping logistics. We are a small group of privacy technologists and entrepreneurs. The core team are U.S. citizens. Our business model is bootstrapped. We have no exit plan. No venture capital. No outside entities to compromise our core beliefs and ethics. Our identities are not published simply because we strive for privacy in our own lives and extend this principle to our clients. You wont find us on LinkedIn, Facebook, or any other social media platform (except Reddit). Sorry no headshots of slick and hip C level execs.
We share a common concern for the exponential progression of capital surveillance and how invasive it is in our daily lives. The information collected about us triggering an algo on a impending purchase is also analyzed by state actors collecting information on their target bypassing due process because it is “public information”.

We are also concerned about shipping interdiction. Citizens and businesses are advancing their privacy and security methods. Online hacking and social engineering practices to compromise our data privacy are more difficult. For example strong, unique passwords and 2FA are becoming the norm. As we become smarter, privacy invasion state sponsored attacks will become more targeted. We proceed assuming parallel construction, supply chain attacks and shipping interdiction techniques are the norm rather than exception.
Our decision is intentional and principled. We avoid or mitigate supporting centralized and privacy invading business models whenever possible. We also do not want to create a dependency on these payment methods to mitigate the risk of being financially de-platformed.
Another principled decision. We are advocates and champions of the Monero business model and baked in privacy by default design. In our opinion Monero is the only private crypto currency meeting our strict privacy requirements. However, we do support bitpay transactions for those preferring to balance convenience with privacy.
Ammunition ordering will be considered in the future. We just need to build out the private supply chain and implement the process and mechanisms. When we do offer ammunition ordering it will be limited to states and regions having no restrictions.
No because we will become a virtual mailbox service. This process will break the chain of privacy. We will be required to legally identify you as a person and your address. We defer these requests to virtual mail box service partners sharing our respect for privacy.
No. Not at this time. This is a re-mailer service however we love the concept and may offer it in the future if requested by our members.
A supply chain attack is where a item is exploited by a bad actor in the process of manufacture and shipment. This attack is most often unknown to the manufacturer and never to the purchaser.
Interdiction is a sub category of a supply chain attack. Interdiction is a nation state term for the process of intercepting something in transit, exploit the item with hardware or software spying devices and send the compromised item to the unknowingly targeted entity.
Parallel construction is a common "legal" investigation process to discover and construct a secret and separate evidentiary process that is often illegal or infringing on the due process rights of the accused. The process is never intentionally disclosed in the evidentiary process. An example would be a law enforcement agency analyzing illegally collected domestic surveillance information to discover or build a stronger case against the target. The illegally acquired information if critical for the case may be documented as a "anonymous" tip.
OSINT is an acronym for Open Source INTelligence. This refers to all the information about the target that is publicly available such as Facebook, LinkedIn, Twitter, credit reports, credit card transactions, municipal public records, published data hacks, etc. The sources are limitless and expansive. It is a very powerful method to collect information on the target. Many tools exist to scrape and crawl the internet, subscription based data collection services, and other digital sources to compile and map the data creating a digital dozier and social graph of the target.
COMING SOON!
© 2020 PrivacyPost.io. All Rights Reserved